Behind Closed Screens
We wouldn’t keep our living room curtains wide open for the world to look into our lives, yet when it comes to our digital lives, we generally act oblivious to the fact that we are giving away a vast amount of information to 3rd parties freely. Partly because we are sold the illusion that everything we do online is between us and our screens.
Initially, the internet was an open forum for connection and information. Very quickly, that information (our information) became extremely valuable, and now every click, keystroke, swipe and even look at a page is tracked.
According to the World Economic Forum the value of the personal data industry is estimated to be a staggering $500 billion - 1 trillion per year.
In the modern age of digital data exploitation, your privacy has never been more critical, and yet many believe it is already a lost cause. It is not. Your privacy is up for grabs, and you need to care about it. Privacy is about power, and it is so important that this power ends up in the right hands.
In the digital age, an increasing amount of personal data is being collected about us. This data is collected by various entities for various purposes, but the potential consequences of having so much personal information exposed can be significant.
From identity theft to government surveillance, it is crucial for everybody to take steps to protect their personal information and maintain their privacy.
To be clear this is not about going dark but rather having sovereignty over the data and information that we leak constantly in the new technological age.
The general response to this issue is :
“BUT I have nothing to hide”
Or
“They already know everything about me anyways"
Let's break this down into what it really means..
1- Privacy is a human right.
Article 12 of Universal Declaration of Human Rights states: “No one must be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honor and reputation.”
It’s a human right just like the right to equality, to justice, freedom, a nationality, the right to religion, etc.
In its current form, most of us don’t actually realise what information we are giving away for the sake of convenience.. There is a reason why companies like Google are happy to provide so many services for “free"

2- Having nothing to hide is not true nor realistic.
Don’t confuse privacy with secrecy. I know what you do in the bathroom, but you still close the door. That’s because you want privacy, not secrecy.
You already have a passcode or some sort of security on your phone. The same goes for email. Nobody ever handed me their phone to allow me to read their chats or see their pictures. If you didn’t have anything to hide, you wouldn’t care. But you do. Everybody does. Privacy is something that makes you human.
Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.”
3- Unpredictability of The Future
The unpredictability of the future is a reason to care about your privacy, as your data could be weaponised in ways you can’t predict. Companies and governments already use it for targeted ads and surveillance. As AI advances, risks like automated profiling—where your data shapes unfair job, loan, or legal decisions—will surge (remember what happened in Minority Report??).
Protecting your personal information now can help ensure it’s not used against you in the future.
4- Privacy is not about going dark
The purpose of protecting our online privacy is not to be completely dark and anonymous online - this is unrealistic and almost impossible, and not the goal. It is about being intentional about who controls your online life.
Progress over perfection is the mantra of protecting privacy. Every little step we take and habit that we change helps to protect ourselves in the fast changing technological world that is clearly moving towards a more inquisitive and controlling state.
Examples of privacy leaks and threats:
We could, in this section, go through hundreds of cases where companies have been hacked, sold or misused our data. So much so that it is almost guaranteed that your data has already been compromised in some way - you can check where you have been compromised :
Instead, let's focus on Google… a company whose services we all use daily.
What does Google track about me ? (https://www.safetydetectives.com/blog/what-does-google-know-about-me/)
Google keeps more tabs on its users than even the most disorganised web user has open on their browser. This includes many different kinds of information, such as:
- Location data, search history, and website visits, even in Incognito mode
- Tracking information and cookies from websites, which can reveal personal details
- Email, document, and photo data stored in the Google cloud, often without proper encryption
- YouTube watch history, used to personalize video recommendations and ads
- Device data, such as battery usage and app activity, from Android phones
- Personally identifiable information, like name, email, and phone number, used to guide searches and ad interactions
- Ad interactions, including skipped or watched ads, to determine future ad targeting.
But we can trust Google with all our data right???
Google has received a significant number of requests for user data from various governments. In the first half of 2024 alone, Google received over 82,000 requests from U.S. federal agencies and other government entities. This trend reflects a growing demand for user information by governments worldwide.
The disclosure rate for user data requests varies by company. Google has a compliance rate of approximately 72.9%. This means that Google complies with about 73% of the requests it receives for user data. The issue to worry about here is that Google doesn’t encrypt the data that you store in the servers, this makes photos, emails and all information you uploaded a target.
(Alternatives for all these services which better help protect your information are available..)
While Google does not directly sell data, it does share information through its advertising systems. Here are the main ways Google utilizes user data:
- Real-Time Bidding (RTB): Google participates in a complex advertising auction system where advertisers bid for ad space. During this process, user data such as browsing history and demographics are shared with multiple advertisers. Although advertisers do not pay for the data itself, they receive insights that help them target their ads effectively.
In the RTB process, sensitive information can be disclosed to numerous companies involved in the ad auction. This includes:
- Device identifiers
- Cookies
- Browsing history
- Location data
It’s not just about Google:
In this example, we looked in detail at how we interact with Google and what potential implications that can have, but this is just one service that we all use daily. A similar exercise can be done with other large & small tech companies e.g Apple, Meta , Amazon etc.
As we will discuss further this article is not advocating readers to stop using Google altogether, rather to consider alternatives and be aware of the trade-offs when we choose convenience and ease over managing our data online.
Where do I even start protecting my privacy?
First we need to understand what we are protecting, and that involves understanding 3 key features:
Privacy vs Anonymity vs Security
These terms are often confused with each other, but understanding their differences is important to protecting yourself online.
- Privacy is controlling who has access to your personal information.
- Anonymity means being unidentifiable, allowing actions without revealing your identity.
- Security involves protecting your data from unauthorised access.
Protecting privacy and staying secure online seems daunting - however once we break it down and accept that we will never be able to protect everything, we can take easy steps that fit into our individual usage behaviours to ensure that we are at least taking some control of our online lives back...
Balancing security, privacy, and usability is one of the first and most difficult tasks you'll face on your privacy journey.
In the case of privacy, using the correct tools and software makes this journey easier and convenient (and yes they exist .. it just requires making a conscious effort to try something new..)
Take, for example, cookie consent forms. You may encounter these dozens of times per day on the various websites you visit, with a nice array of checkboxes and sliders which allow you to "curate" your preferences to exactly fit your needs. In the end, we just hit the "I Agree" button, because we just want to read the article or make a purchase. Nobody wants to complete a personal privacy audit on every single website they visit. This is an exercise in choice architecture, designed to make you take the easy route out instead of delving into a maze of configuration options that don't need to exist in the first place.
But what if your browser and search engine did the hard work for you ?
3 Step process:
Step 1: Create a threat assessment:
- What are the areas of my online persona that are most sensitive and how can I take steps to initially protect further leaking of data.
Step 2: Do the easy things first
Change your browser and search engine :
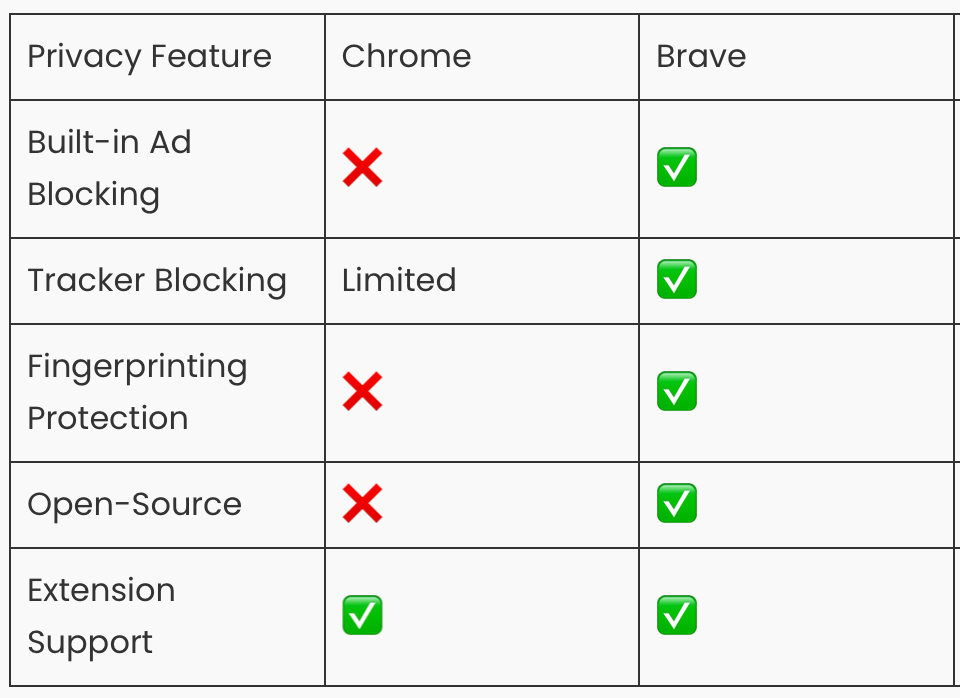
Having a privacy-respecting browser helps protect you from websites that collect more data than they should. It reduces tracking, safeguards your personal information, and minimises your digital footprint while you browse.
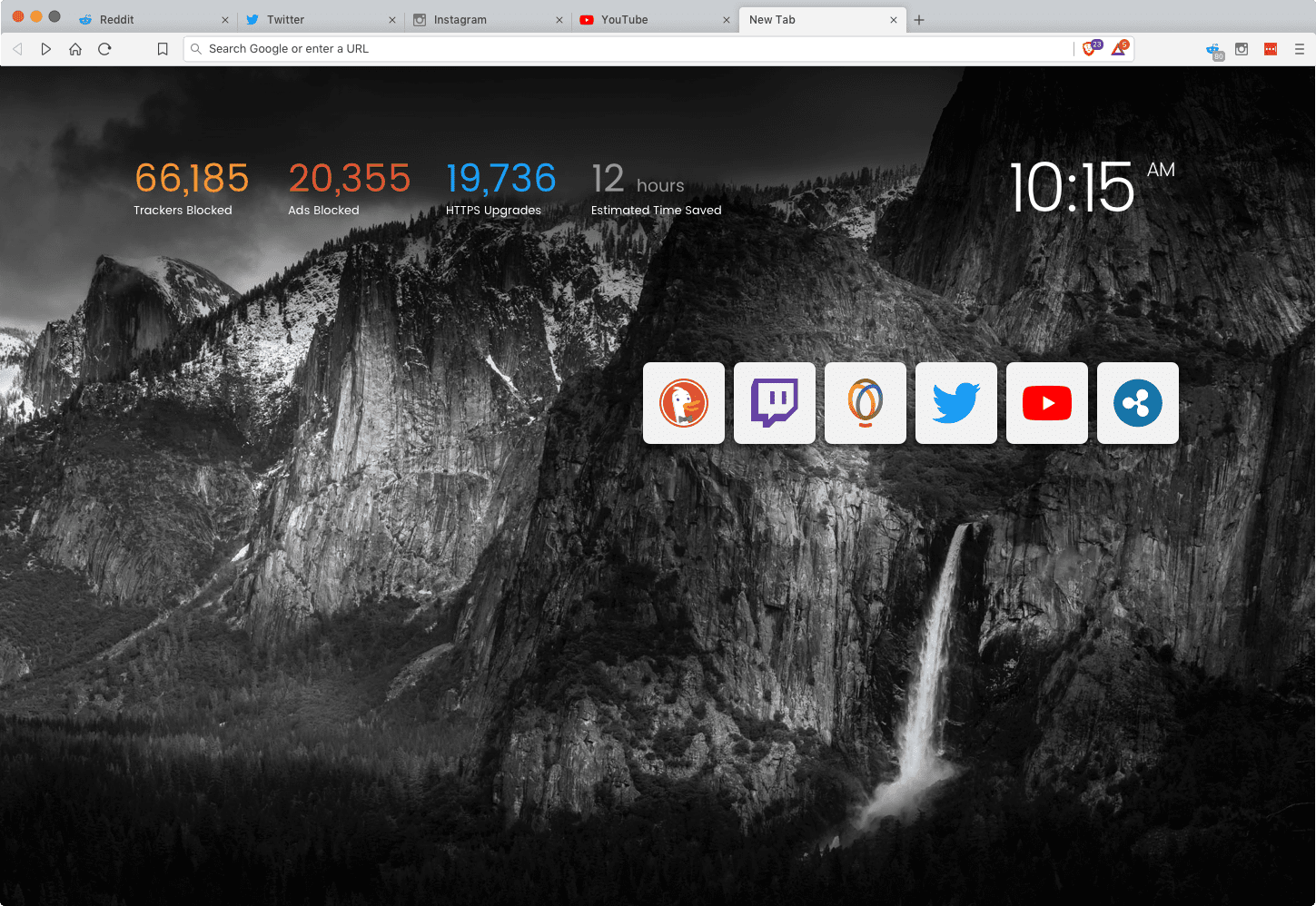
For example Brave and DuckDuckGo browsers automatically block cookies and ads as well as protecting your privacy while searching on the internet.
Brave is excellent for out-of-the-box privacy since it blocks ads and trackers automatically. Brave Browser also comes with Brave search engine, which protects your search history - Google Chrome as we discussed, monitors all of this information.
This simple step of using a new search engine and browser has very little impact on user experience but go a long way to protecting your search data.
Brave vs Google Chrome browser:
Email services:
Consider using more secure email services where your mails are encrypted. Also consider having alias addresses for website sign-ups
- Proton Mail is a privacy focused alternative to Gmail for your more sensitive information and projects :
- When it comes to security and privacy, Proton Mail takes the lead. With end-to-end encryption, your emails are completely private. This means only you and the recipient can read your messages – no one else, not even Proton Mail itself. Also, Proton Mail is based in Switzerland, which has some of the strictest privacy laws in the world, so solid legal frameworks protect your information.
Gmail, on the other hand, doesn’t offer end-to-end encryption by default. It uses standard encryption while emails are being sent, Google has access to your emails since they are stored on their servers and aren’t encrypted. If privacy is a big concern, this could be an issue. Gmail also scans emails for ad targeting, which means your data is used to personalize ads and services. While Gmail has strong security, the lack of encryption and its data-sharing practices don’t stack up when compared to Proton Mail’s privacy-first approach.
Proton Mail allows users to create aliases, which are additional email addresses that can be used to send and receive mail while keeping your primary email address private. Users on paid plans can create multiple aliases, and all Proton Mail users can create unlimited aliases by adding a "+" sign to their username.
This is particularly useful to use alias email addresses when signing up to websites.
Messenger Services:
At the moment, Whatsapp has a seemingly unassailable monopoly over web based messenger services. The thought of the lost messages and media that we have built up over the years presents a daunting thought of moving to an alternative.
In 2025 we actually learnt that the US government uses Signal for communication, after a journalist was accidentally added to a Signal chat.
Accidental additions of people aside, the news has got regular folks asking if they should, too, be using Signal for private communications.
Probably the largest alternative to Signal, WhatsApp is owned by Meta, and has faced criticism for its data-sharing practices.
But is switching to Signal truly an improvement? Let’s explore the differences between these apps and whether the move would be justified.
Both WhatsApp and Signal offer end-to-end encryption, ensuring that only the sender and recipient can read messages. But the difference is that Signal employs “Sealed Sender,” a feature that hides metadata even from itself, whereas WhatsApp collects metadata such as phone numbers, IP addresses, and device information, which it shares with Meta and third parties.
As president of Signal Meredith Whittaker said in a statement to Dutch website Security.nl:
“WhatsApp collects and shares, when required, large amounts of private information that is not encrypted, like your profile picture, your location, your contacts, when you send a message, when you stop, who’s in your group chats, and so on.”
Signal collects minimal data, but it’s run by the non-profit Signal Foundation, which operates free from commercial interests. Signal’s open-source code allows for public scrutiny of its security claims, which is a transparency WhatsApp lacks.
This is a harder switch for us all to make and it also requires a network effect of our friends and family making a conscious shift to protecting more of our data. This is something we can all at least download and look to switch slowly over time. Be the pioneer amongst your friends to make the hard change.

Step 3: Prioritise privacy going forward and slowly move towards a more secure online future.
Managing our online footprint initially starts with a recognition of the problem and then taking small steps and changes to how we use the internet. In the age of AI and surveillance, it is now crucial that we don’t wait longer to make these changes. Data is and will continue to be used against users both commercially and in some cases maliciously.
The importance of protecting our online privacy cannot be overstated. As we've seen, companies like Google collect vast amounts of personal data, which can be used for targeted advertising, surveillance, and even sold to third parties. The value of the personal data industry is estimated to be over $500 billion, and it's clear that our data is a valuable commodity. However, by taking control of our online lives and making conscious choices about the services we use, we can protect our privacy and maintain our autonomy in the digital age.
By understanding the differences between privacy, anonymity, and security, and taking simple steps such as using a privacy-respecting browser and search engine, we can start to reclaim our online privacy. Alternatives like Brave, DuckDuckGo, Proton Mail, and Signal offer more secure and private options for our online activities.
While it may seem daunting, every small step we take towards protecting our privacy is a step in the right direction. By prioritizing our online privacy and taking control of our data, we can ensure that our personal information is used in ways that benefit us, rather than being exploited for the gain of others.
Resources to learn more about online privacy:







Member discussion